Research Activities
Publish Articles
Open Source Projects
Research Vulnerabilites
Participation in CTF
Cybersecurity Online Training
Anon Cybersecurity Group (Unk9vvN) decided to create a comprehensive and complete online educational platform for the activists and those interested in these fascinating sciences in Iran and also in Middle Eastern countries due to the remarkable growth of cybersecurity sciences in the world. This educational platform has been developed with the best content quality and educational standards in the world, and it is supposed to operate in six key areas of penetration testing, red team, industrial security, digital criminology, blue team and security audit.

Latest Blogs and Webinars
Web Penetration Testing Roadmap
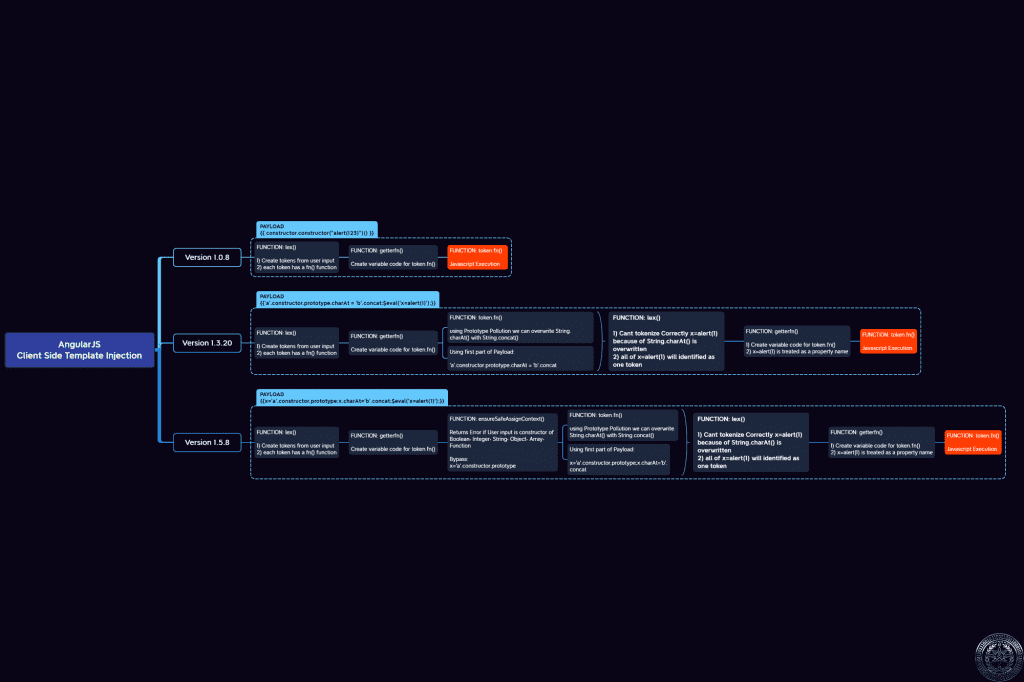
Client Side Template Injection into AngularJS
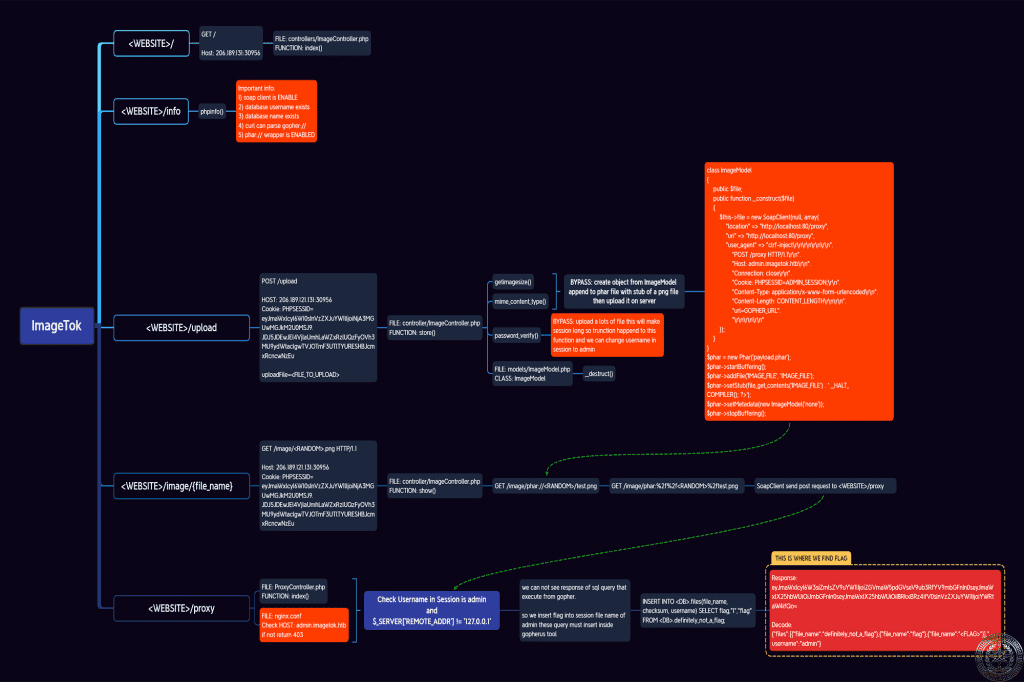
Writeup ImageTok Challenge in HackTheBox
Some of our Customers







Offensive Simulation
One of the solutions to increase the level of security in an organization is to implement various scenarios of advanced cyberattacks in a simulated way and using a combination of penetration testing expertise and red team we are able to assess all vulnerabilities and defects of defense security infrastructure. These assessments are based on the techniques that Advanced Persistent Threat teams use to anonymize and invisible their files, which allows the Security Control Center (SOC) to be evaluated to respond Predictable to a real attack. This can greatly help to recognize behavior of real attackers.
Bug Hunter
Bug hunters always seek to discover vulnerabilities and focus on coding mistakes, so using the potential of bug hunters along with other security mechanisms can be a suitable option to discover holes that are the main cause of an attack. Are cyber Bug bounty programs use the same strategy, and companies take full advantage of the potential of bug hunters in addition to all their mechanisms. Our research team always participates in CTF competitions and bug bounty programs. It strengthens itself in this field, so you can enter our bug discovery programs that are offered exclusively to customers.
Defensive Operation
One of the requirements of any organization is to use defensive solutions, it means that along with the deployment of defense services such as NIDS \ HIDS and EDR, the potentials of the experts should be used. Experts in the field of defense security are divided into the blue team and forensic. Blue team experts set up, configure and monitor the defense mechanisms. The digital forensic team is a complementary that is responsible for threat hunting and gathering threat information. Another task of forensic teams is to perform reverse engineering, which neutralizes ransomware if used in the attack.